Protecting your data against cyberattacks
Labgroup guarantees its clients protection from any ransomware attack due to highest security standards.
The current events of ransomware attacks hit over 300 000 computers around the world infiltrating banks, hospitals and government institutions.
Labgroup is pleased to inform its clients that no incident of a cyberattack or ransomware attack has been registered/reported. No client of Labgroup, using cloud computing (only for managed services), content & records management or data protection services, has been affected by these recent incidents.
Labgroup constantly improves its security measures while investing in high malware prevention solutions. The result, a complete protection against malicious software! The information lifecycle management company is proud to confirm that to this day, Labgroup has not been infiltrated or affected by a cyberattack.
What is ransomware?
The ransomware is distributed by emails, infecting the computer of the recipient. The software encrypts all files and a ransom is asked to be paid. The ransomware further attempts to infect other machines on the same network. In the specific case of ransomware “Wannacry”, the infection spreads without any user interaction, using a Windows vulnerability on a commonly used network protocol.
 Ransomware can:
Ransomware can:
- Prevent you from accessing your data.
- Encrypt files so you can’t use them.
- Stop certain apps from running (like your web browser).
Why is malware so effective?
Most of us have already experienced a typical spam mail in our email account, containing an attached file (with a non-common extension) or URL link, suspicious at first sight.
New cyberattacks are more sophisticated, working with .pdf extensions and even files containing just a part of the malicious software code to deviate antispam/virus software.
Rather than sending the code within one file, which is (often) automatically detected by a standard antivirus/spam system, the malicious software code is sent in parts, integrated into non-suspicious, for instance, .jpeg or .pdf files and non-detectable by standard antivirus software.
If opened, the part of the code is silently installed on your computer, waiting for the other pieces of the malware puzzle to be integrated. Once all pieces of the puzzle are installed, they merge into one single code, infecting the computer of the victim.
How does Labgroup ensure a complete protection to its clients?
 In order to guarantee a complete protection against cyberattacks, Labgroup implemented different solutions and follows strict security processes on several levels.
In order to guarantee a complete protection against cyberattacks, Labgroup implemented different solutions and follows strict security processes on several levels.Labgroup constantly invests in its security systems, so it seemed only natural to work with this pioneer in the field of malware prevention by integrating ODI Share and ODI Mail into its protection system. ODI offers a next generation threat neutralisation and removal process based on advanced heuristics and mathematical algorithms, originally developed for the military and specially created to protect companies, like Labgroup, against malware.
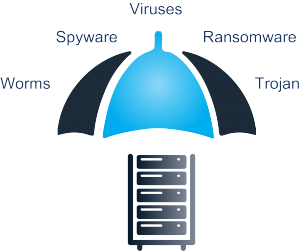
Functional backups are highly recommended to restore your files easily.
Backup is done incrementally and automatically to ensure minimal network resources while also safeguarding user productivity. In the case of a cyberattack, your data can be restored safely using our IT Recovery service.
For further information, download the brochure here.
What should I do when managing devices by myself? Click here.